Why it matters: Police departments in at least three states have issued warnings regarding a new feature in iOS 17 called NameDrop. Officials say it is a security risk because it could release your contact information to bad actors near your phone. However, it's not as insecure as they would have you believe.
You might remember the "Bump!" app if you are a long-time iPhone user. Launched in 2009, it allowed users to fist bump to trade contact cards, photos, or other data from one device to the other. It did not use near-field communication (NFC). Instead, Bump servers handled the exchange. The company and app went defunct in 2013.
Ten years later, Apple reintroduced the functionality in iOS 17. While it uses NFC, it is not as insecure as Ohio, Oklahoma, and Pennsylvania authorities are trying to portray it. The Washington Post notes that Sophos Security Specialist Chester Wisniewski calls the warnings "hysteria" and "nonsense."
Those issuing the warnings appear to be unaware of precisely how NameDrop works. It is not as simple as walking up to someone with a phone in their back pocket and stealing their information by moving your phone close to theirs. The exchange requires user interaction.
NameDrop automatically starts when two iPhones running iOS 17 come within a few centimeters of each other for about two seconds. The phones can connect while locked, but both users must unlock their phones and tap the notification to make the exchange. It is also limited to only the contact sheet. Furthermore, users can uncheck any information they do not want shared, such as home address or birthdate. The exchange then takes place once each user hits the confirmation.
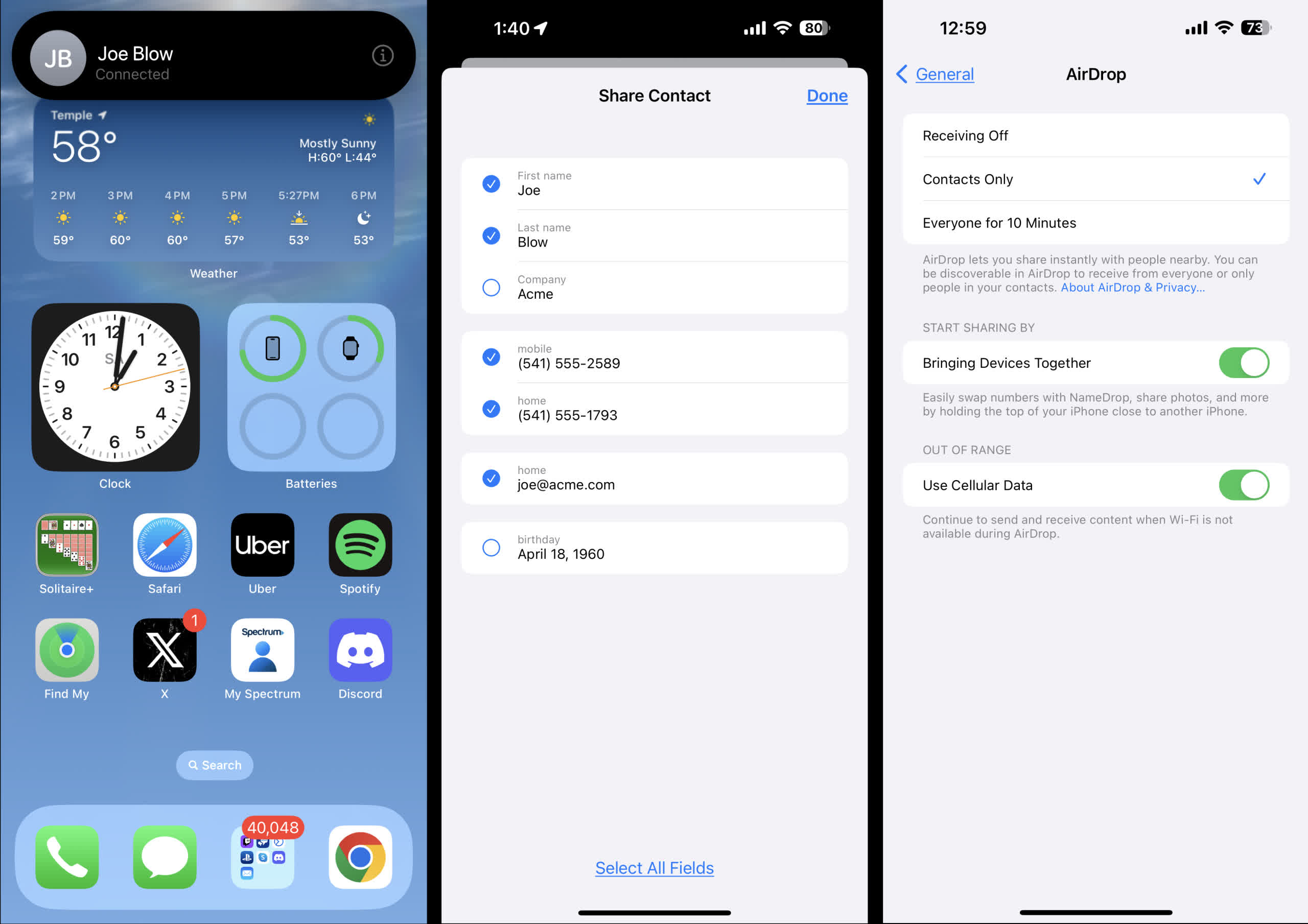
So, for scammers to steal your data, they must have physical access to your iPhone and know the unlock code. If they have that, then NameDrop is not even necessary.
NameDrop is not the only time law enforcement has issued fear-mongering warnings about tech before having any facts to justify the cautionary statements.
In 2018, a British researcher devised a way to deliver malware via a USB-C Apple charger. The technique became known as "juice jacking."
The following year, the district attorney for Los Angeles put out an advisory urging travelers to avoid using USB charging stations, like those found in airports, for risk of becoming infected with malware. However, authorities could not cite a single juice-jacking incident occurring outside of a security lab.
More recently, the FBI issued a similar warning in April, again without any precedence of it ever happening in the wild. And there is a good reason nobody can find any examples of such an attack occurring--there are far easier methods of distributing malware than sneaking into an airport and hijacking its charging kiosks.
Hackers can be clever and find unique ways to carry out bad deeds, but when it comes to practical application, they are just like everybody else. They will take the most efficient and easy way to accomplish a task rather than a more complicated and risky route. So don't fear NameDrop.
That said, the feature is simple to disable. Navigate to Settings ->General->AirDrop. Then toggle off the switch next to "Bringing Devices Together." Disabling this setting also turns it off on your paired Apple Watch.
